Implementation and General Overview of VLAN Trunking Protocol (VTP)
By Michael Keller. Senior Consulting Engineer at Aspire Technology Partners
Introduction
VLANs are a core component of networking and are critical in their utility spanning across a plethora of architectures, including Data Center, Wireless, UC and just about every base switching architecture there is. Their importance in networking goes without saying. They are still the cornerstone of any enterprise core, distribution, and access-switching architecture.
With that in mind, it’s vital to understand the fundamentals of VLAN Trunking Protocol (VTP), as it can make or break an enterprise if misconfigured.
Let’s dive in and look at VTP and understand how it works.
Problem Statement
In enterprise situations where layers of defunct engineering work have accumulated over years and years, it’s imperative to have an optimal VLAN architectural layout, which also involves optimizing the propagation of how VLANs traverse from device to device. It can be difficult or tricky when you have a medium to large-scale enterprise with many switches – especially when it involves keeping track of them.
Background
At its core (no pun intended), VTP is just what it stands for: a protocol designed to steady and control the flow of VLANs advertised in an enterprise. VTP is enabled by default on Cisco switches, with the care and shaping of its configuration as our focus today. This is particularly helpful for engineers not experienced in working with VTP. It is also a Cisco propriety protocol – key to note if an enterprise contains third-party hardware or switches of a non-Cisco variety, which can cause issues or breakpoints in a network segment if not configured or correctly understood at a minimum.
VTP has three modes, each with unique effects on an enterprise: Server, Transparent, and Client mode. The advertisement/transmission of VLANs from switch to switch is predicated on a specific, manually defined VTP domain in which certain switches in that enterprise segment exist and when the VTP is first configured. This is also true as it corresponds to the version of VTP used, VLANs that exist or need to be configured, etc.
Let’s look at each and how they work, as well as other mechanics related to VTP holistically.
VTP Server Mode
Within the framework of an enterprise, the VTP Server should effectively always be configured on the core switch(es). This is largely due to the fact that the VLAN framework is managed at the core (which also typically handles the inter-VLAN routing). Consequently, VLAN advertisements from the VTP server propagate throughout all the enterprise switches.
The most important thing to remember is that in server mode, you can create, change, and remove VLANs. Any device participating in VTP using the same domain in the server will receive these VLAN advertisements from the server. As such, it’s important to consider that server mode is especially important depending on the way your enterprise is set up.
VTP Client Mode
Any switch that operates in VTP Client mode essentially acts in a “passive” manner, collecting VLAN advertisements from the server, and populating its database with all VLANs traversing inter-switch trunks to other client switches. It’s important to note that this comes with risk since you don’t necessarily want an IDF switch across campus to share VLANs with another area of the network, or even if Layer 2 is stretched across a longer distance.
Client mode tends to make managing VLAN advertisements a bit easier for the administrator since there’s no requirement to enter VLANs on a switch manually. The important thing to remember is that synchronization of VLANs in the same domain is critical, and as architectures get a bit more complex in non-collapsed core environments, so too does VTP setup, as well.
VTP Transparent Mode
In VLAN Trunking Protocol (VTP) transparent mode, a device does not advertise its VLAN information to other VTP devices and does not participate in the VTP domain. The device will not receive or process VTP advertisements from other devices and will not send its own VTP advertisements.
However, the device will still pass VTP advertisements to other devices, allowing them to communicate and synchronize their VLAN configurations. The transparent device will also update its local VLAN configuration based on received VTP advertisements, allowing it to communicate with VLANs configured on other VTP devices.
Transparent mode is useful when you want a device to communicate with VLANs configured on other VTP devices but do not want it to advertise its local VLAN information or participate in the VTP domain. This mode can be useful in cases where you want to add a device to an existing VTP domain but do not want to change the VTP domain’s configuration or disrupt its operation.
VTP Domain
VTP domains consist of one or more switches in an enterprise that shares a common administrative name. You may have switches that exist together geographically on campus connecting to a single distribution switch, and you want to “group” these switches together in the same VTP domain.
When a switch receives an advertisement over a trunk (or an interface that passes multiple VLANs from switch to switch), it will assume the management domain name, as well as the VTP configuration revision number. This is a “learned” process by switches, and thus it is imperative to configure switches into their appropriate domain where VLAN advertisement can be controlled in a structured fashion from switch to switch.
For example, consider for a second that your CIO wants to partition two segments of the campus into separate domains for geographic redundancy or disaster recovery. Under these circumstances, you may need to reconsider how VTP is set up from a domain perspective initially since it’s possible you could use two different VTP domains under these circumstances. Just some food for thought.
VTP Password
An additional measure of security, VTP passwords are simply a “key” that is like a VTP domain, in that the key must match between devices wherever it is used. This is optional, of course, but it does add another layer of protection for your VTP setup. Oftentimes, administrators tend to forget VTP passwords since sometimes they’re rarely changed, so just make sure that information is kept secure. Passwords are optional and manually added and are not mode-specific.
VTP Pruning
Pruning is critical as it pertains to VTP. As the “trunking portion of the name indicates, setting up trunked uplinks between switches in an enterprise requires careful consideration. This is especially true when using VTP since you control which VLANs are passing in between switches. Pruning restricts the VLANs flow, improving overall performance by minimizing flooding traffic over inter-switch trunked uplinks.
VTP Versions
There are three different versions of VTP: v1, v2 and v3, each with their own unique characteristics that one should consider before setting up.
The chart below outlines VTP and the characteristics for each version:
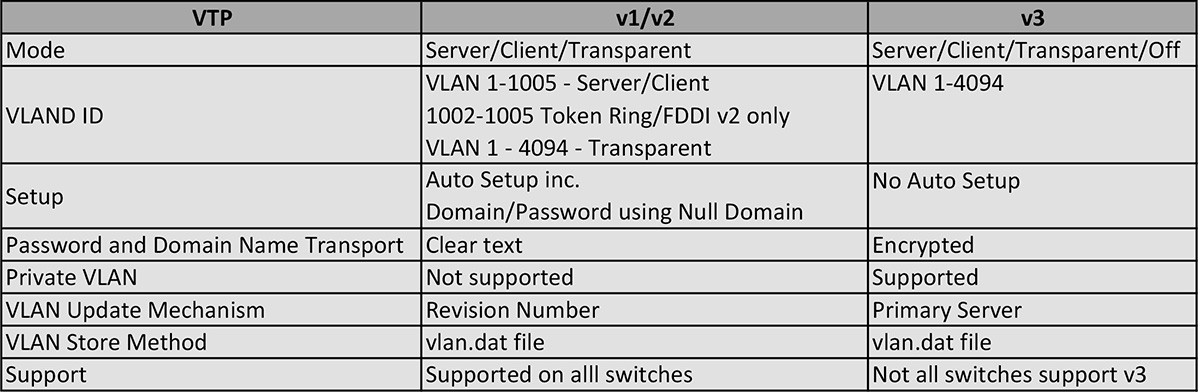
As noted above, there are a variety of factors involved in the different versions of VTP. Things such as private VLANs and the VLAN update mechanisms are only supported in v3. The revision number is the key element in how VLANs get updated. From a security perspective, v1 and v2 also utilize clear text for password and domain name transport, whereas in the more secure v3, they are encrypted.
It is important to note that not all switches support VTP v3, so refer to Cisco documentation on the hardware you run to ensure v3 is available for use. It is also important to note that VTP v1 is the default version out of the box.
Solution
Knowledge is the key to utilizing VTP within any enterprise’s framework. You must understand the fundamentals, operability and repercussions if misused. Keep VTP in mind when deploying new or existing switching architecture. Used properly, it can enforce the secure advertisement of VLANs to their appropriate locations.
Conclusion
VTP is one of the oldest and most unheralded aspects of enterprise networking and certainly one of the most widely troubleshot protocols when there’s a suspected issue involving switches. It can make or break an enterprise if incorrectly configured and thus requires a thorough understanding and review if already put into service.
Since inter-switching connectivity is the bread-and-butter base of any network, understanding the flow of VLANs and how you can better strengthen your environment is crucial in short and long-term financial and daily troubleshooting overhead.
References
- “What Is VTP In Networking” https://afrozahmad.com/blog/vlan-trunking-protocol-what-is-vtp-in-networking/
- “What are the VTP Modes?” https://www.geeksforgeeks.org/what-are-the-vtp-modes/#:~:text=There%20are%20three%20VTP%20versions,only%20VLANs%201%20to%201005.
- “VTP Modes and Versions: VTP v1, VTP v2 and VTP v3” https://ipwithease.com/vtp-mode-and-version-comparison/
- “VTP v1, VTP v2 and VTP v3” http://secureitnetworks.net/wp-content/uploads/2017/02/Screen-Shot-02-01-17-at-10.42-PM.png
- “Configuring VTP” https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3560/software/release/12-2_52_se/configuration/guide/3560scg/swvtp.html

Aspire Technology Partners is a Cisco Gold Integrator and Gold Provider engrained in solution pillars that set us apart as a true Cisco solutions provider. We are committed to the continuous improvement of expertise and skillsets around Cisco initiatives that enable us to help and guide customers in the adoption and management of technology architectures designed to transform their organization. We hold Cisco Master Specializations in Collaboration, Enterprise Networking, and Security and are one of only 25 partners in the US to receive the Cisco Advanced Customer Experience Specialization.